Mascot security – guest users and administrators
Mascot Security is a role-based access system that allows administrators to control different aspects of privacy and priority access. It integrates with authentication systems like Microsoft Active Directory (AD) and various single sign-on systems. It can also be configured for a core lab, where search results can be shared with collaborators without them having access to the results of other groups.
This time I am going to describe a different kind of access configuration. This is a minimal and unobtrusive configuration where anyone with access to the Mascot Server can run a search and review results without having to log in, but only administrators can make changes to the configuration files. This can work for a research lab that is not sharing the results outside of the lab or otherwise needs to restrict access to the search functions of the server. In that case, you might wonder why bother with security at all. If everyone has access to all the Mascot configuration options, then changes can be made, particularly changes to global settings, that affect all Mascot Server users. For example, if changes are made to the way modifications are searched, your results won’t have been run under identical conditions anymore.
The default guest user settings allow access to the help pages and run a PMF search, and that is about it. The edited guest permissions below offer far more access than the default permissions. Let’s start by enabling security. Open a command prompt or shell on the Mascot Server and change to the mascot/bin directory. Enter the command:
For Linux:
./enable_security.pl
For Windows:
..\perl64\bin\perl.exe enable_security.pl
Now log in as an admin. After enabling Mascot security, the admin password is reset to admin. When you log in, you will be required to set a new admin password. Once past that hurdle, we can configure the guest user account.
A quick note: If you want to turn Mascot security off, open a command prompt or shell on the Mascot server and change to the mascot/bin directory again and then enter the following command:
For Linux:
./disable_security.pl
For Windows:
..\perl64\bin\perl.exe disable_security.pl
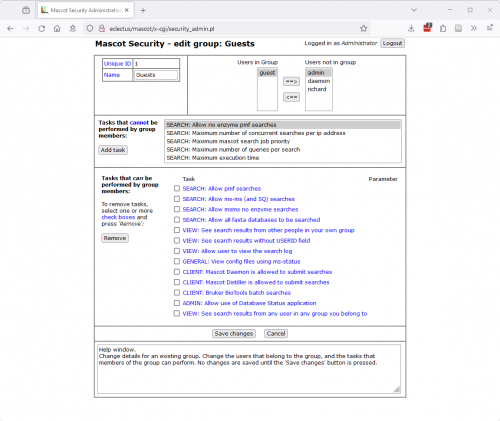
Back to the task at hand. With security enabled, go to the Configuration Editor->Security editor. Select “Guest” under “Groups” and click edit. Add and remove tasks so that the settings look like this:
- SEARCH: Allow pmf searches
- SEARCH: Allow ms-ms (and SQ) searches
- SEARCH: Allow msms no enzyme searches
- SEARCH: Allow all fasta databases to be searched
- VIEW: See search results from other people in your own group
- VIEW: See search results without USERID field
- VIEW: Allow user to view the search log
- GENERAL: View config files using ms-status
- CLIENT: Mascot Daemon is allowed to submit searches
- CLIENT: Mascot Distiller is allowed to submit searches
- CLIENT: Bruker BioTools batch searches
- ADMIN: Allow use of Database Status application
- VIEW: See search results from any user in any group you belong to
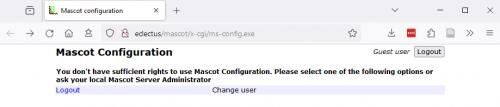
Save the changes. From this point onward, only the admin user can access the configuration editors. When a guest tries to access the configuration editors, Mascot security prevents it:
If you don’t want to distribute the admin password to everyone in the lab, you can create named users and add them to the admin group. By default, administrators can’t run searches so the only time someone will need to log in is to add a new database or a custom modification or otherwise change the settings.
Another way to seamlessly log in to Mascot Server is by using Microsoft Active Directory (AD) or various single sign-on systems. When the user logs in to the operating system, their credentials are also used to log in to Mascot Server. This is straightforward to implement but does require support from the local IT group.
This leads me to an administration tip. Most of the configuration changes made to the Mascot Server are recorded in the mascot/logs/config.log file. It can be opened with a text editor like Notepad. This allows the computer administrators to review any changes to the settings. If you have added named users as administrators, you can track who made the change. Mascot Server also saves a back up configuration file after each change so it is easy to roll back to a previous configuration if need be. Changes to Mascot Security users and groups are not currently recorded and the user.xml and group.xml files are not backed up automatically, so it’s a good idea to review your backup and disaster recovery procedures.
If you have any questions about Mascot security please let us know at support@matrixscience.com.
Keywords: configuration files, security, sysadmin